Drlogy
Healthcare organization
Why Data Security Feature Must In Patient Portal Software
Data security features in patient portal software are essential for protecting sensitive patient information from unauthorized access and breaches.
Check:
They ensure patient privacy, build trust, and comply with regulatory standards, ultimately safeguarding the integrity of the healthcare system.
Check:
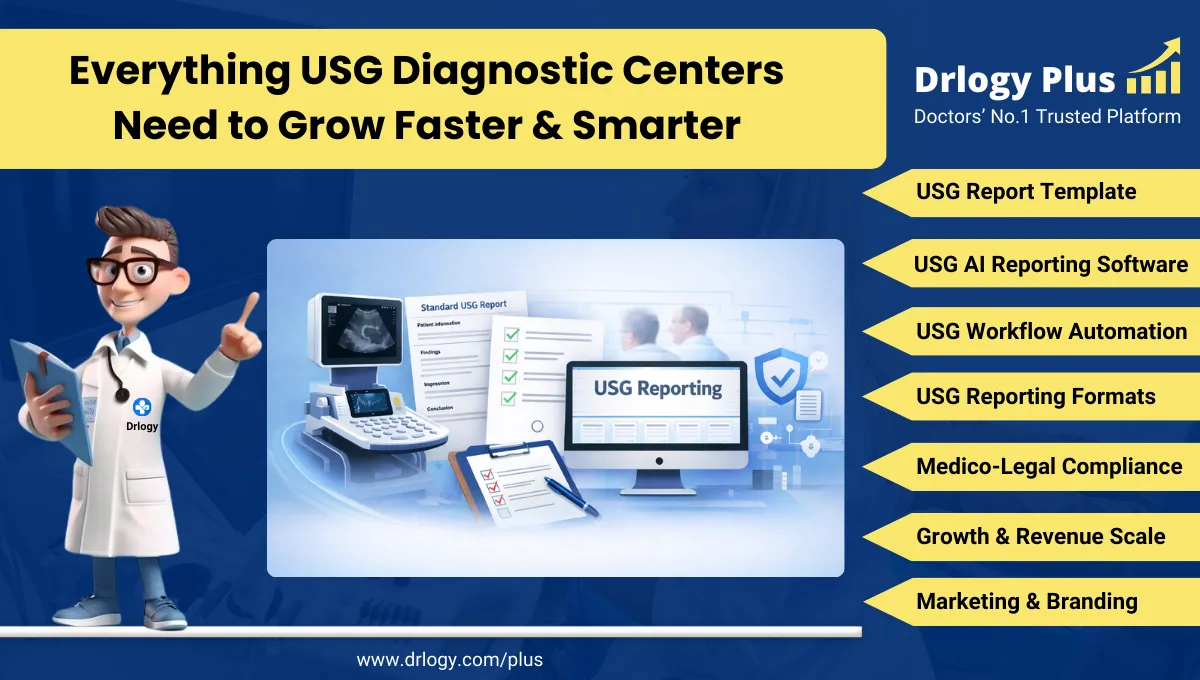
10 Best Data Security Features for Patient Portal Software
Here are 10 Best Data Security Features for Patient Portal Software.
1. Secure Authentication
Your data is well-protected through secure authentication methods that include:
- Strong Passwords: Requires complex passwords, reducing the risk of unauthorized access.
- Two-Factor Authentication: Adds an extra verification step, making it harder for unauthorized users to access your account.
- Session Timeout: Automatically logs you out after inactivity, preventing unauthorized access if you forget to log out.
- Biometric Verification: Allows secure and convenient logins using fingerprint or facial recognition.
- Access Controls: Ensures that only authorized personnel can view your sensitive information, based on their users and permissions.
2. Encrypted Data Transmission
Your personal health information stays confidential during online interactions through:
- Data Encryption: Protects your data as it's transmitted to prevent interception by unauthorized parties.
- Secure Communication Channels: Utilizes safe channels for data transfer, ensuring your information remains private.
- End-to-End Encryption: Keeps your data encrypted from the moment it leaves your device until it reaches its destination.
- Protects Personal Information: Safeguards your sensitive health details during all online activities.
- Compliance with Standards: Adheres to strict industry standards for encryption, ensuring the highest level of data safety.
3. Data Access Monitoring
You can trust that access to your data is monitored with:
- Access Logs: Tracks who accessed your data and when, ensuring transparency and accountability.
- Alert System: Notifies administrators of any unauthorized or unusual access attempts to your data.
- Regular Audits: Periodically reviews access logs toentify and fix potential security issues.
- Activity Reports: Provides detailed reports on who accessed your data and what actions they took.
- Accountability Measures: Ensures that all access to your data is linked to individual user accounts, making it easy to track who is responsible for any actions.
4. Secure Messaging
Your communications with healthcare providers are kept safe through:
- Encrypted Messages: Ensures that all messages are encrypted, keeping them secure from unauthorized access.
- Message Authentication: Confirms the authenticity of messages, protecting against impersonation and fraud.
- Access Restrictions: Limits who can see your messages, safeguarding sensitive information.
- Secure Archiving: Stores messages securely, preventing unauthorized access to historical communications.
- Alert Notifications: Alerts you to any suspicious or unauthorized messaging activities, ensuring your communication remains secure.
5. Data Backup and Recovery
Your data is protected against loss with:
- Regular Backups: Ensures that your data is regularly backed up to prevent loss in case of a system failure.
- Data Restoration: Provides reliable options to recover your data quickly in emergencies.
- Backup Encryption: Keeps backup copies of your data encrypted for added security.
- Disaster Recovery Plan: Implements a plan to maintain your data's integrity during unforeseen events.
- Safe Storage: Stores backup data in secure locations to prevent unauthorized access.
6. Secure Access Controls
Access to your sensitive information is strictly regulated with:
- Role-Based Access: Limits who can view or modify your information based on their, ensuring only authorized personnel have access.
- Permission Settings: Customizes access levels for different users to control who can see what.
- Regular Reviews: Keeps access controls up-to-date to ensure ongoing security.
- Access Approval Process: Requires approval for changes in access permissions, preventing unauthorized alterations.
- User Authentication: Verifies userentity before granting access to your data, ensuring only you and authorized personnel can access it.
7. Data Privacy Policies
Your privacy is protected by clear policies and practices, including:
- Privacy Statements: Clearly outlines how your data is collected, used, and protected.
- Informed Consent: Ensures you are informed and consent to the use of your data according to privacy policies.
- Data Usage Transparency: Provides transparency about how your data is used and shared.
- Opt-Out Options: Allows you to opt out of certain data uses or sharing practices, giving you control over your information.
- Privacy Training: Educates staff on privacy policies to ensure your data is handled responsibly.
8. Secure Data Storage
Your data is securely stored with:
- Protected Storage Systems: Uses secure systems to store your data, preventing unauthorized access.
- Data Segregation: Keeps your data separate from other types to minimize risk.
- Access Restrictions: Limits who can physically or digitally access storage systems to authorized personnel only.
- Secure Deletion: Ensures that data is securely deleted when no longer needed, preventing unauthorized recovery.
- Data Integrity Checks: Regularly checks stored data to ensure its integrity and prevent corruption.
9. Patient Data Anonymization
Yourentity is protected through anonymization techniques such as:
- Data Masking: Masks your sensitive information to protect yourentity during data sharing or analysis.
- Anonymous Reporting: Allows your data to be used for reporting and analysis without revealing yourentity.
- Controlled Data Access: Ensures anonymized data is used in a way that does not compromise your privacy.
- Anonymization Tools: Uses advanced tools and techniques to effectively anonymize your data.
- Compliance: Adheres to regulations and standards for data anonymization, ensuring your privacy is maintained.
10. Incident Response Plan
In case of a security breach, your data is protected through:
- Preparedness: Maintains a plan to address potential security breaches quickly and effectively.
- Rapid Response: Ensures a swift response to any data security incidents, minimizing potential damage.
- Communication Procedures: Sets up clear procedures for informing you and other stakeholders about incidents.
- Post-Incident Review: Conducts reviews after any incidents toentify causes and improve security measures.
- Ongoing Training: Provides continuous training for staff on incident response procedures, ensuring they are always prepared.
Drlogy Patient Portal Software Features Guide
Here's a full guide for 14 best Patient Portal Software features for labs.
| 1. Appointment | 8. Patient Dashboard |
| 2. Billing | 9. Health Records |
| 3. Lab Results | 10. E-Prescription |
| 4. Secure Messaging | 11. Data Security |
| 5. Communication & Sharing | 12. Patient Education |
| 6. Mobile App | 13. Patient Feedback |
| 7. Report Tracking | 14. Patient Followup |
Summary
Overall, Data security features in patient portal software are crucial for safeguarding patient information, ensuring privacy, and maintaining trust between patients and healthcare providers.
Check Drlogy Patient Portal Software Features Guide for efficient inpatient management and enhanced patient care for your labs for better patient management.